Video shared early on public blog. Public on channels after creation of coversheet / thumbnail.
click below to watch on decentralized peertube
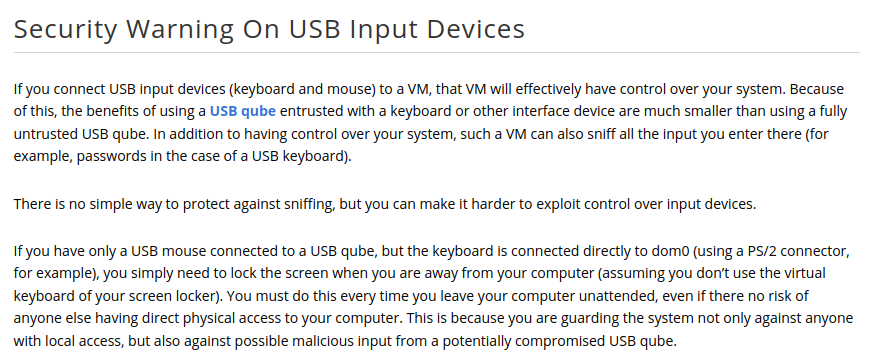
Qubes Documentation Security Notes:
EXAMPLE: TOUCHSCREEN ACROSS QUBES
Open file for your usb hardware (can use this post for other hardware). For our example, it relates to the tablet touchscreen.
Edit usb device file. In this case:
FILE: /etc/qubes-rpc/policy/qubes.InputTablet
Your file may hold similar location, depending on hardware.
FILE CONTENTS:
sys-usb dom0 allow
The above allows usb device across Qubes.
Another example requires answering ("ask") prior to usage.
In this case, you may fill /etc/qubes-rpc/policy/qubes.InputTablet with:
sys-usb dom0 ask,default_target=dom0
$anyvm $anyvm deny
Regardless of the file variation (you decide on), reboot after saving.
Enjoy touchscreen Qubes.
Thank you to new owner of Qubes tablet, inspiring video. Continuing to share tutorials, based on things I'm working on. Thanks for everyone's support making independent content.
🤝 Help Support This (funds public servers / tutorials / videos)

