
I've had numerous followers mention home machines and networks compromised in the last year alone.
Problem with one compromised device is: many times it leads to others (especially when sharing the same network).
The following short story / example includes safety practices I was taking today (maybe I'll make a public dedicated video on this topic, but at the moment, sharing while on my mind).
STORY: Working on a custom security-related usb stick (series coming soon).
I needed to boot into said disk for additional testing / work.
My main machine was playing a (quite long) interview (one I was quite enjoying).
Wasn't quite ready to shut things down (to boot into this disk).
THE GOAL: multi-task
THE PROBLEM: my most trusted machine was busy.
I needed to go in and edit this disk while main laptop played this video.
In this instance: I needed a 2nd x86 computer to work on the disk (booted).
Directly next to me sat a laptop - one I hadn't had chance to inspect / work with.
I Asked Myself: should I use this unfamiliar laptop to edit the disk?
Answer: No.
In fact I have no idea (at all) what may (or may not) be on the computer closeby - used by who knows who in the past (as article details, even new machines have been discovered to have malicious firmware).
UNKNOWN COMPUTER DANGERS: If a computer is set in a malicious way (whether new / used), it could snag encryption passphrases used to unlock disks / authenticate.
Even if unlikely (luck would be this bad), it's entirely possible.
Or copy information, obfuscated in later transmission.
Advanced attackers can infect your entire network: starting with a single exploitation: especially if you were to use said disk on multiple devices (or later attack via a jump-point: of the initially compromised machine) - even if airgapped.
Airgap: security standard where machine, or series of machines are offline / not connected to networks (minimizes ability of machines to exploit one another). Mass infection takes place by sharing a maliciously infected disk (or even a single networked machine).
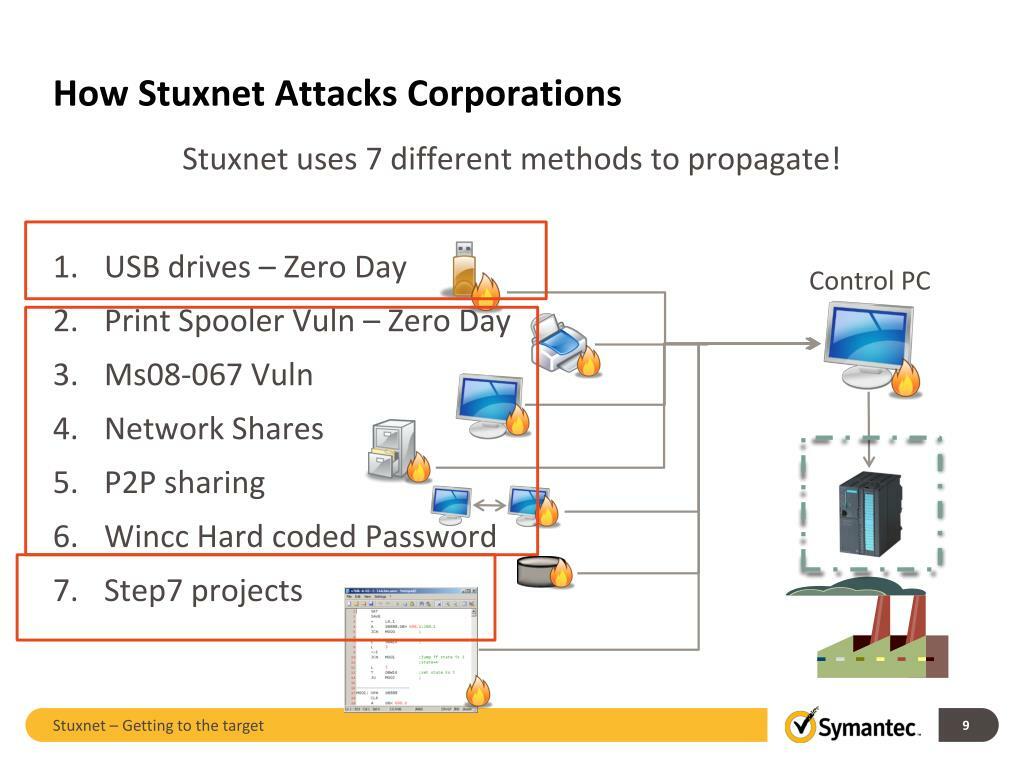
REAL-WORLD EXAMPLE: STUXNET

SEE: STUXNET (real-world example for malicious usb stick)
TIP: handling secure storage, whether operating system, or otherwise, only unlock on the machine/s trusted most.
For our (intended to be) most private / secure set up, use caution before testing devices we are less familiar with.
TIP: don't use security-minded disks on friends / publicly used computers.
LIMITS OF MALWARE
Malware can act out in innumerable ways. Since we can't predict this, better safe than sorry (especially working on something that handles sensitive personal apps / files).
TIP: As I've mentioned in previous videos one option is to create / use multiple different purposeful device set ups, each with their own identity / common goal.
Some devices may (for example) have their own identity / alias (ie: for your privacy). Covered lightly in the backdoors video, offering a couple basic examples on having a different dedicated device for different purposes.
Example: One machine (or virtual machine even) for one alias (ie: to protect from databrokers). Another machine for the next - that one may sound an extreme example for some.
But it keeps things organized / secure using a minimalist access approach (alternative being something like Qubes).
TIP: to enhance security: add some level of separation.
Compartmentalize your most secure device AWAY from where you might try out "new downloads" from github (for example) - or use a sandbox, or virtual machine.
Another example (as mentioned in that video): You may have one machine for communication, another for finances, etc.
Doesn't have to be this complicated - I'm simply stating: keep at least one device where you take less chances. Never know when you might need this.
SIMPLE TIP: add a "burner account" to your linux system.
COMMAND: adduser testing
(select this user during login when testing something you are unsure of)
While this won't be quite as "fool-proof" (as isolating an entirely dedicated piece of hardware), it minimizes risk to the local device (as long as you isolate all other activity with relatively secure permissions).
By adding a 2nd "burner account" (such as "testing" login), you restrict testing activities to that home directory. Still depends on a reasonably secure system to prevent local exploitation possibilities.
Use this to try out things you aren't quite sure of (and use this account for nothing else). Linux will prevent that user from writing to sensitive files (if malicious, and overall system permissions set properly).
THE POINT: for devices you want "secure", avoid strange software found outside the official Linux repositories / sources (apt-get / pacman).
Use any of the following options to enhance your security / privacy experience: sandboxing, virtual machines, or even: multiple "burner accounts" on your Linux install (created specifically for this purpose).
If you found this post interesting / useful, why not share it? Thank you.
Sharing links help this blog / channel move up into recommended search results. Your help sharing content is greatly appreciated.
Thanks for following. It's free (support options).
