
Being a developer in IT company means working in different projects with your professional laptop or if you are a freelancer you are also in the same situation, having multiple projects in your machine.
Some project is hosted in private Git, other in Public Git like GitHub / GitLab / Bitbucket / Azure DevOps…
As a developer we have neither time nor memory to set user & password every time we want to push our commit, the best solution is to use Git with SSH method.
What is an SSH KEY?
An SSH key is an access credential for the SSH (secure shell) network protocol. This authenticated and encrypted secure network protocol is used for remote communication between machines on an unsecured open network. SSH is used for remote file transfer, network management, and remote operating system access. The SSH acronym is also used to describe a set of tools used to interact with the SSH protocol.
SSH uses a pair of keys to initiate a secure handshake between remote parties. The key pair contains a public and private key. The private vs public nomenclature can be confusing as they are both called keys. It is more helpful to think of the public key as a “lock” and the private key as the “key”. You give the public ‘lock’ to remote parties to encrypt or ‘lock’ data. This data is then opened with the ‘private’ key which you hold in a secure place.
How to Create an SSH Key
SSH keys are generated through a public key cryptographic algorithm, the most common being RSA or DSA. At a very high level SSH keys are generated through a mathematical formula that takes 2 prime numbers and a random seed variable to output the public and private key. This is a one-way formula that ensures the public key can be derived from the private key but the private key cannot be derived from the public key.
To generate SSH Keys in Mac / Linux and Windows (use Git Bash) is the same, you have to run following commands:
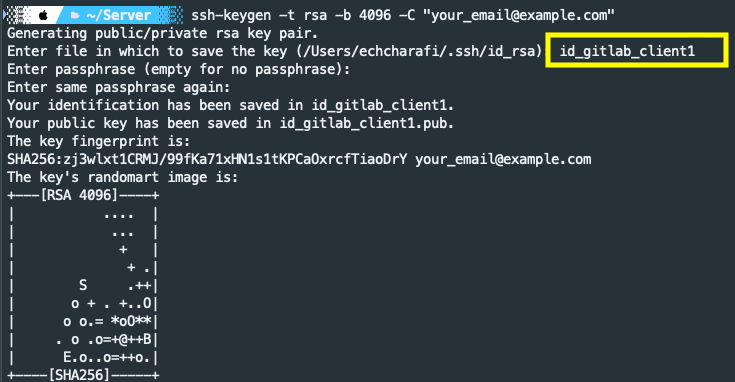
ssh-keygen -t rsa -b 4096 -C "[email protected]"This command will create a new SSH key using the email as a label
You will then be prompted to “Enter a file in which to save the key.”
You can specify a file location or press “Enter” to accept the default file location.The next prompt will ask for a secure passphrase.
A passphrase will add an additional layer of security to the SSH and will be required anytime the SSH key is used. If someone gains access to the computer that private keys are stored on, they could also gain access to any system that uses that key. Adding a passphrase to keys will prevent this scenario.
Many developers accept suggested name or add only a unique number to separate between different ssh key, at least we have multiple SSH keys, and we don’t have any idea they are used where !
I suggest using a meaningful name to have a better organization of our SSH-keys.
To add your public key to GitLab / GitHub / Bitbucket / Azure DevOps… you have to copy the entire file “id[FILENAME].pub” and paste into your Git Server:
GitLab: https://gitlab.com/profile/keys.
GitHub: https://github.com/settings/keys
Bitbucket: https://bitbucket.org/account/settings/ssh-keys/
Azure DevOps: https://dev.azure.com/[PROJECT_NAME]/_usersSettings/keys
Everything is great now, we do the configuration of git with ssh very well, and we can push / pull / fetch with a simple commands without any user & password every time.
Problem N°1
I integrate in new project with another Git Server (GitLab), I was very happy about my SSH Method in the first project (GitHub) & I need to do the same in my new project, so I generated the key & added to GitLab, but Git CLI don’t work anymore !
Don’t panic, the solution is very easy we need to create a relationship between our SSH-keys public file & Git Server, to do that let’s create git config.
$ vim ~/.ssh/configadd the following code:
Host github.com
HostName github.com
User git
AddKeysToAgent yes
IdentitiesOnly yes
UseKeychain yes
IdentityFile ~/.ssh/[YOUR_GITHUB_ID_RSA_KEY]Host gitlab.com
HostName gitlab.com
User git
AddKeysToAgent yes
IdentitiesOnly yes
UseKeychain yes
IdentityFile ~/.ssh/[YOUR_GITLAB_ID_RSA_KEY]Save file & run Git command in new project, everything work great 😎😎.
Problem N°2
I’m so happy about my new skill, I work on many projects with SSH Method & everything is great.
But yesterday I integrate a new project hosted in GitHub too, so I generated my SSH keys & edited my ssh config to create the relationship between my new ssh key & my host, but I have the same errors as Problem N°1, I don’t understand why !! 😔😔
The problem is very simple Git didn’t understand which host you mean about your new ssh key file, to do that we need to create a custom host :
$ vim ~/.ssh/configadd the following code:
Host github-client2.com
HostName github.com
User git
AddKeysToAgent yes
IdentitiesOnly yes
UseKeychain yes
IdentityFile ~/.ssh/[YOUR_GITHUB_CLIENT2_ID_RSA_KEY]now change your git origin to the new custom host:
for new project:
$ git clone [email protected]:my_team/my_project.gitfor cloned project:
$ git remote set-url origin [email protected]:my_team/my_project.gitThank you 🙏
You can now extend your support by buying me a Coffee.😊👇
Thanks for Reading 😊
